- SOLUTIONS
- SERVICES
Clients are kept up-to-date on the progress and outcomes of tasks or deliverables, but they are not directly involved in the work or decision-making process.
Consulting allows us to share our insights and suggestions to improve the quality or outcomes of the project or deliverable.
Projects can be business optimizations with tasks, timelines, milestones, and outcomes.
A Managed Service Provider (MSP) is a company that offers various IT services to help your business run smoothly and efficiently.
A Managed Security Service Provider (MSSP) offers comprehensive cybersecurity solutions to protect your business from online threats.
- TRAINING
Training Categories
- MARKETS
- ABOUT
- RESOURCES
- Verify Explicitly
- Least Privileged Access
- Assume Breach
Read the Microsoft ZTA adoption report to gain more insight into the main concepts associated with a ZTA and digital empathy.
The goal of ZTA deployments are to secure all threat vectors related to the new hybrid workspace that has emerged as a result of the shift in work due to the COVID-19 pandemic.
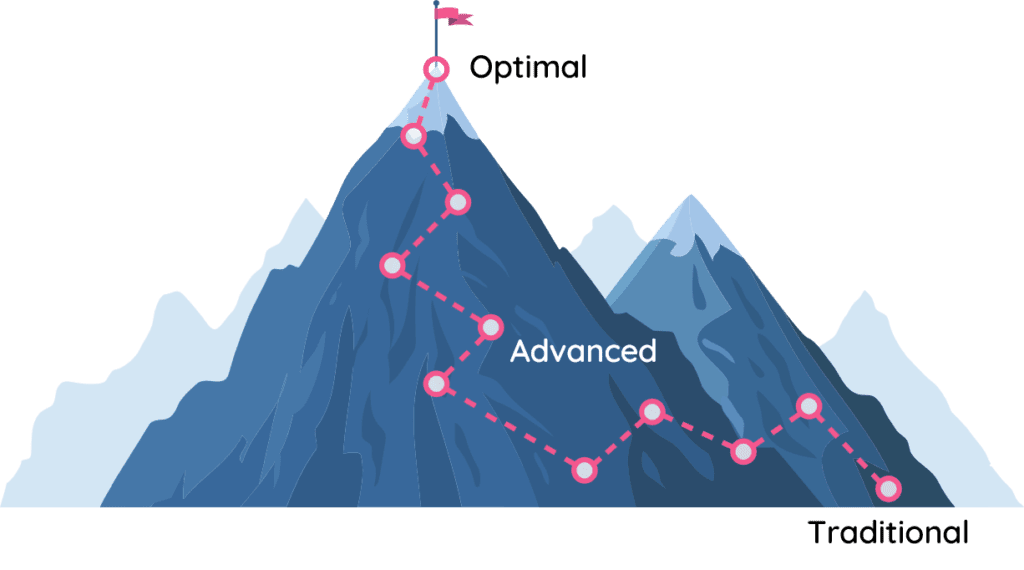
JADEX believes that applying a ZTA to your entire digital landscape is only possible through the use of Microsoft technologies and services. Implementing a ZTA will require a comprehensive plan with foresight and vision. First, you must prioritize milestones and assets.
START YOUR JOUNEY
It doesn't matter where you are on your journey. Every step forward will reduce risk!
Company Details
- DUNS Number: 078570307
- CAGE Code: 6TX26
- NAICS Codes: 541690, 541990, 541611, 54618, 611420, 541370, 541519
Contact
- HQS - Spring Lake, MI
- Phone: 1 (833) 568-3925
- Email: info@jadexstrategic.com
Codes & Certs
- VOSB - self-certified
- SBA 8(a) - pending








