- SOLUTIONS
- SERVICES
Clients are kept up-to-date on the progress and outcomes of tasks or deliverables, but they are not directly involved in the work or decision-making process.
Consulting allows us to share our insights and suggestions to improve the quality or outcomes of the project or deliverable.
Projects can be business optimizations with tasks, timelines, milestones, and outcomes.
A Managed Service Provider (MSP) is a company that offers various IT services to help your business run smoothly and efficiently.
A Managed Security Service Provider (MSSP) offers comprehensive cybersecurity solutions to protect your business from online threats.
- TRAINING
Training Categories
- MARKETS
- ABOUT
- RESOURCES
SIEM/SOAR/XDR
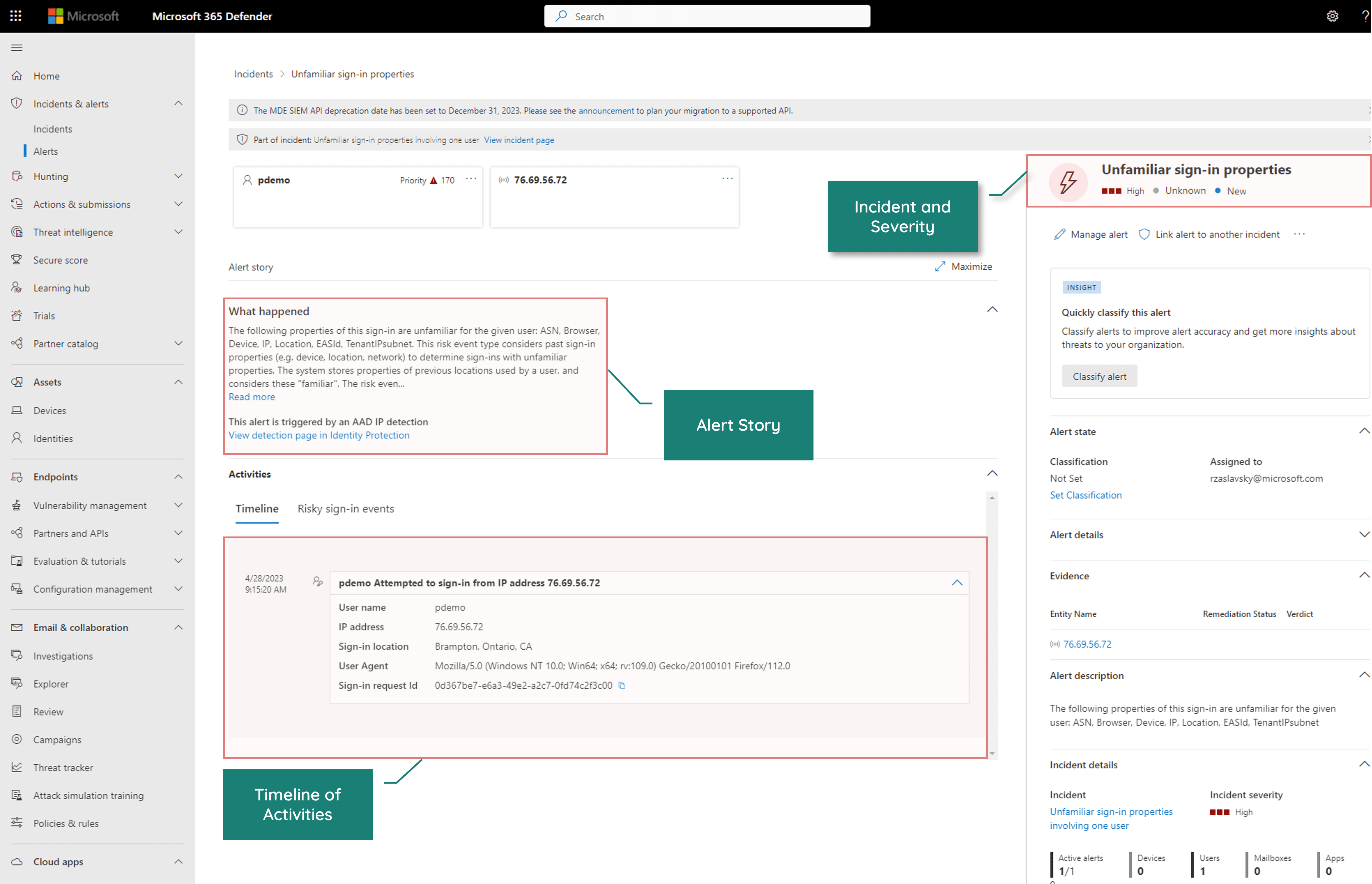
Microsoft 365 Defender and Microsoft Sentinel enable best-in-suite, enterprise-grade cybersecurity operations for any business.
What is the solution?
Microsoft Sentinel
Is a revolutionary security information and event management (SIEM) / security orchestration, automation, and response (SOAR). It enables the collection of security insights across your business while providing the ability to detect, investigate, and automate logical responses that remediate elaborate cyberattacks.
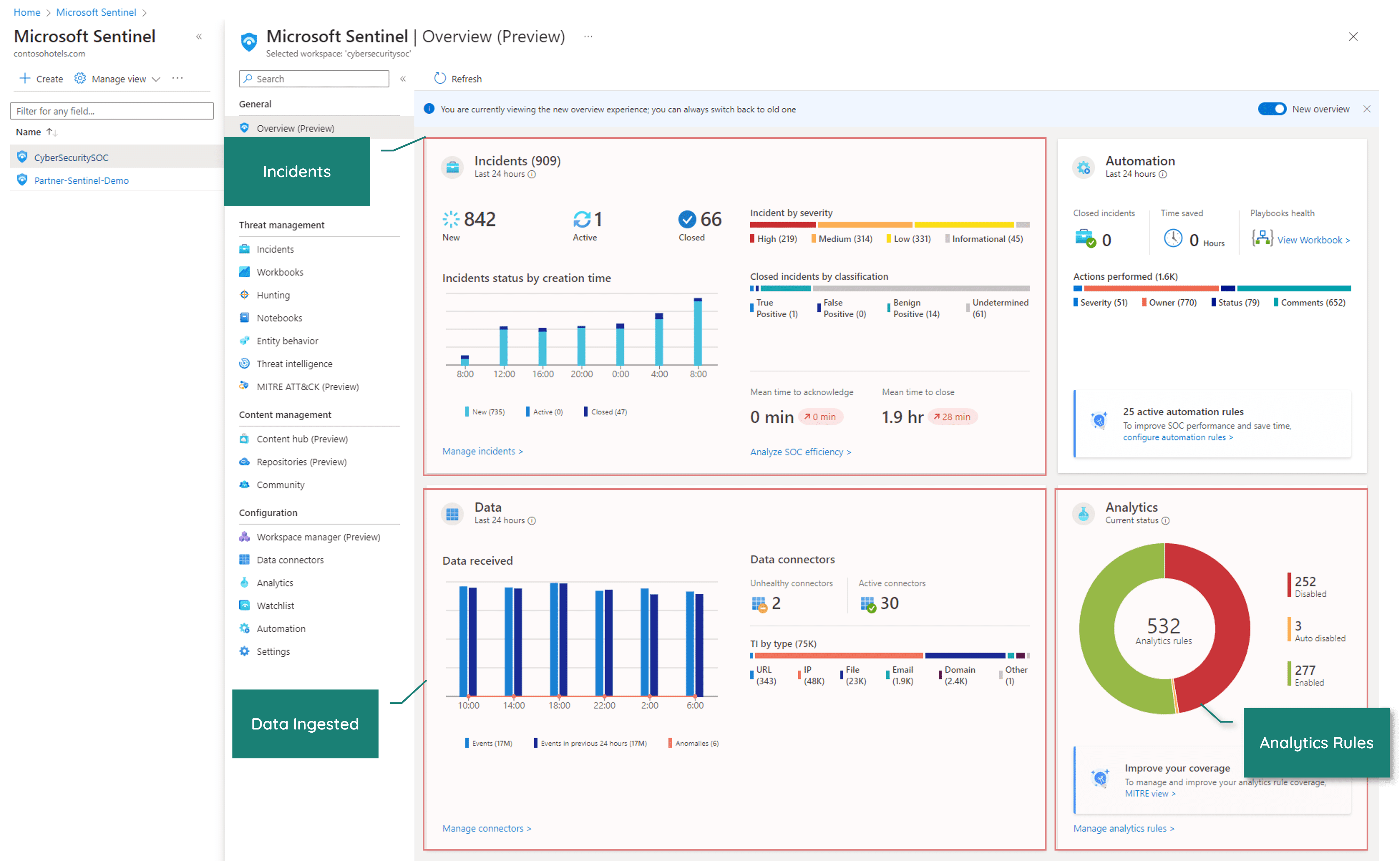
What is the Reasoning?
Collect
Collect data across multiple clouds, on-premises environments, all users, all devices, your entire infrastructure, and all business applications at cloud speed with scalability.
Detect
Detect cyberattacks and security incidents with sophisticated threat intelligence. Uncover attackers in the system by responding to a security alert of irregular activity or proactively pursuing anomalous events in the enterprise activity logs.
Respond
Rapidly respond to security alerts with built-in orchestration and planning of common task automation. When a cyberattack is detected, act rapidly, identify, and investigate whether it is an actual cyberattack or a false alarm.
Investigate
Investigate cyberthreats with Microsoft artificial intelligence (AI) and machine learning (ML) while pursuing attackers for irregular behavior.
Recover
Achieve disaster recovery goals necessary to preserve and restore technology, availability, security, confidentiality, continuity, compliance, and integrity of business services during and after a cyberattack.

For Zero Trust
Zero Trust is a framework that many regulators and businesses rely on for security. A SIEM/SOAR/XDR is essential for complete security monitoring and thorough analyses of your data & technology.
Capabilities & Features
How to implement?
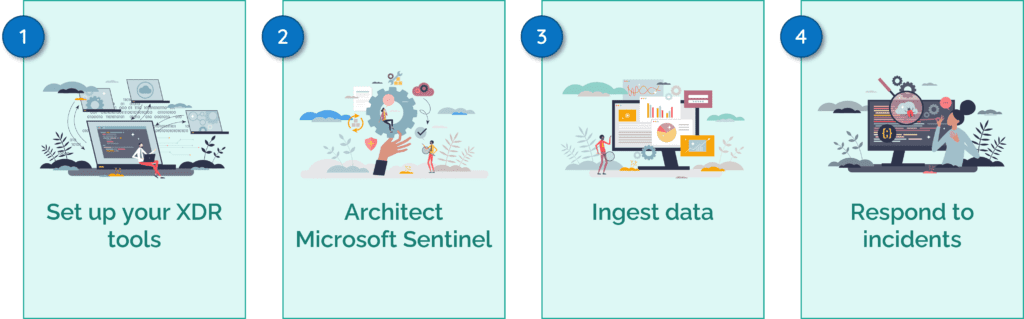
Incident Response
Understand scope and insights from incidents.
Understand the attack, investigate malicious entities, review remediation and prevention measures.
Understand the scope of the cyberattack and record any evidence for security management.
Understand resolutions of cyberattacks with repeatable playbooks and automated orchestration.
Company Details
- DUNS Number: 078570307
- CAGE Code: 6TX26
- NAICS Codes: 541690, 541990, 541611, 54618, 611420, 541370, 541519
Contact
- HQS - Spring Lake, MI
- Phone: 1 (833) 568-3925
- Email: info@jadexstrategic.com
Codes & Certs
- VOSB - self-certified
- SBA 8(a) - pending