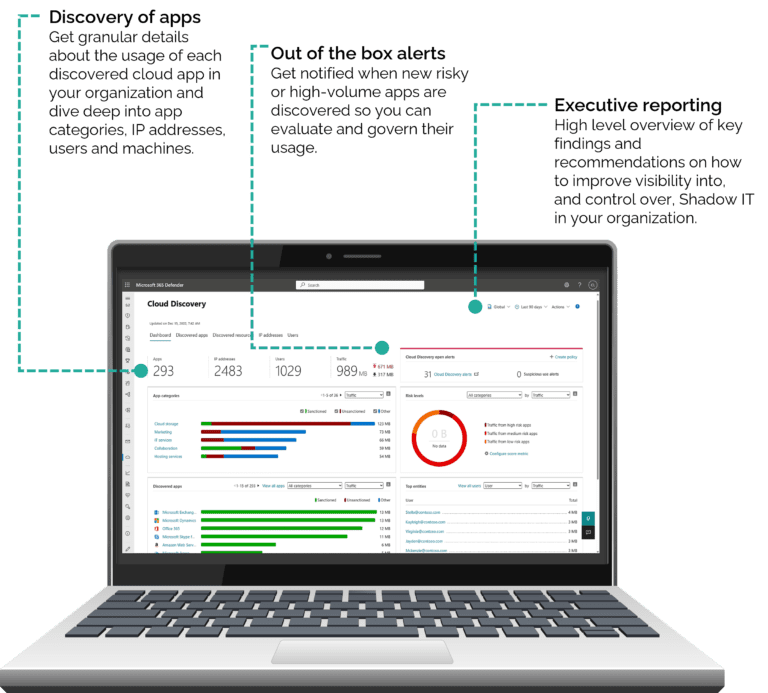
Cloud Security
Microsoft Entra ID (formerly known as Azure Active Directory) is at the forefront of cloud security technology, providing Jadex and its clients with unparalleled visibility into corporate cloud applications and services. By leveraging technology with advanced analytics, we proactively detect and neutralize cyber threats, ensuring robust cybersecurity through seamless integrations within Microsoft’s identity and security solutions. With Microsoft Entra, you can assert control over your data’s consumption, no matter where it resides.