How to Manage Your SaaS Responsibilities and Risks
Introduction
If you run a business, you probably use one or more software-as-a-service (SaaS) solutions from different vendors. In this blog post, I want to explore the implications of this common practice for the shared responsibility model and the shared responsibility matrix that applies to the contract between your business or organization and the service provider.
Example of a SaaS Solution: Microsoft 365
Let’s take Microsoft 365 as an example of a SaaS solution. When someone from your business or organization signs up for this service, they agree to the Terms of Use or Terms of Service that Microsoft has set. This means that they are legally bound by the conditions and obligations that Microsoft has defined.
But what exactly are those conditions and obligations? And what are the responsibilities that you and Microsoft share when it comes to the security and performance of the service? To answer these questions, we need to look at the Shared Responsibility Model that Microsoft has published here.
Understanding the Shared Responsibility Model
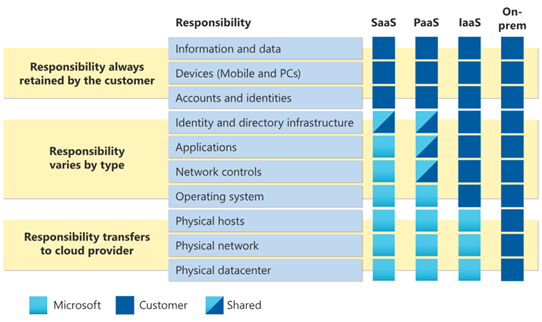
This model shows how the responsibility for different aspects of the service varies depending on the type of cloud service model: SaaS, PaaS (Platform-as-a-Service), or IaaS (Infrastructure-as-a-Service). For this topic, we will focus only on the first column, SaaS. If we examine the items marked with “Responsibility always retained by the customer”, we can see that the customer is always responsible for the following:
- The information and data that they store and process using the service.
- The devices that they use to access the service.
- The accounts and identities that they create and manage for the service.
This means that you, as the customer, must ensure that your data is protected, your devices are secure, and your accounts and identities are properly configured and controlled. Microsoft, on the other hand, is responsible for most of the other aspects of the service, such as the physical infrastructure, the network, the operating system, the application, and the security measures. However, there is one area where you and Microsoft share some responsibility: the identity and directory infrastructure. This means that you must work with Microsoft to ensure that the authentication and authorization mechanisms for the service are aligned with your business needs and policies.
Implications for Your Business Decisions
So, what does all this mean for you, the customer, when you are making decisions related to who should provide Information Technology or Cybersecurity services for your business? For example, how many different SaaS applications does your vendor bundle together to provide their service for your business? Have you had a discussion with your vendor about who is responsible for what?
The reason this is important becomes evident when regulatory requirements begin to affect your business. For instance, if you are subject to the Payment Card Industry (PCI) Data Security Standard (DSS), Criminal Justice Information Services (CJIS) Security Policy, Gramm-Leach-Bliley Act (GLBA) or the California Consumer Privacy Act (CCPA), you need to know how your data is collected, stored, processed, and shared by the SaaS providers that you use. You also need to know how you can exercise your rights and obligations under these regulations, such as the right to access, rectify, erase, or port your data. You cannot simply assume that the SaaS provider will take care of everything for you. You need to understand the shared responsibility model and the shared responsibility matrix that apply to each SaaS solution that you use, and make sure that you comply with the terms and conditions that you have agreed to. Similarly, you cannot assume that your Managed Service Provider (MSP) or Cloud Service Provider (CSP) is taking care of these things either, unless you have explicitly agreed that they are “managing” your environment. Otherwise, the MSP or CSP is fulfilling the task of informing and consulting you, but not acting on your behalf. If you are being managed by an MSP or CSP, then there will be a shared responsibility between both parties, and you need to clarify the scope and extent of that responsibility.
How Jadex Strategic Group Can Help You
Therefore, we recommend that you review the contracts and agreements that you have with your SaaS providers and familiarize yourself with the shared responsibility models and matrices that they have published. You should also communicate with your SaaS providers and clarify any questions or concerns that you have about the division of responsibilities and the security and performance of the service. By doing so, you will be able to make informed and responsible choices for your business and your customers.
One way to simplify your provider options and reduce the complexity of managing multiple SaaS solutions is to select Jadex Strategic Group, a pure-play MSP that only utilizes Microsoft as its vendor. Jadex has proven expertise in understanding where responsibility resides and can improve your overall security posture by providing comprehensive and tailored IT and cybersecurity services for your business. Jadex can help you leverage the benefits of Microsoft 365 and other Microsoft cloud solutions, while ensuring that you meet your compliance and regulatory obligations. If you are interested in learning more about how Jadex can help you, please contact us at info@jadexstrategic.com or 1(833) 568-3925.
Read More Posts ...

The CUI Dilemma for DIB Leaders

Paving the Way for Defense Contractor Success

The Future of Compliance

Cost of Poor Microsoft 365 Deployments

Why Small Doesn’t Mean Simple

The Cybersecurity Imperative

Accelerating Enterprise Growth

Unlocking Excellence
CMMC Compliance Simplified

The Value of Simplicity

Rethinking Managed Services

Strategic Advantages of Cloud-Native Businesses

How Microsoft 365 Drives Real Business Outcomes
Lessons from the Ship to the Server Room

Simplify Compliance, Empower Your Business

Unleashing the Power of Content Management and Collaboration Tools with OneDrive & SharePoint Online
Modern IT Inefficiencies

Internal IT vs. Outsourcing in the DIB

Shaped by Service: A Journey Through Business and Ethics

Empowering Your Business Through Strategic IT Simplification

Choose wisely: The role of device choice in cyber resiliency planning

Empowering Your Business with Tailored IT Solutions

On-device AI and security

Protect Your Most Valuable Asset

Safeguarding Data in Turbulent Times

Underutilization of Microsoft 365

Security Implications of Mass Linux Adoption

Addressing Vulnerabilities with Clear Solutions

What Sets Copilot Apart

Reflecting on Our Journey at Jadex Strategic Group

AI Security Essentials

Empowering High Performers: Strategies for Success in the Public Sector

Maximizing ROI with Microsoft 365 Copilot

Unlocking Business Potential with Jadex Strategic Group and Microsoft Cloud Solutions

The Crucial Role of Scoping

Context a vital role in Cybersecurity and IT Services

Revolutionizing Internet Access and Security with Entra and Global Secure Access

Outsourcing in IT and Cybersecurity: A Double-Edged Sword

The Ethical Approach to Content Marketing in Cybersecurity

Integration with Microsoft Over Vendor Agnosticism

Veterans Are the Hidden Gems of the Modern Workforce

Maximizing Microsoft 365 ROI

Unlocking Remote Work Success: The Critical Role of Defined Objectives

Rethinking the Return to Office: A New Perspective on Remote Work

CMMC Compliance with Microsoft 365

The Myth of Full Responsibility

Understanding Common Security Anti-Patterns: Poor Attention to Ongoing System Care

Understanding Common Security Anti-Patterns: Keeping Security Separate

Common Security Anti-Patterns: Handmade Security

Legacy Systems: A Drain on Resources

Common Security Anti-Patterns: Securing the Cloud as If On-Premises

Common Security Anti-Patterns: Neglecting Essential Maintenance

Enhancing Security and Compliance with Unified SaaS Solutions

Unveiling the Hidden Advantages: My Journey from U.S. Intelligence to Cybersecurity Leadership

Why a Scientist Makes a Good Cybersecurity Expert

How to Manage Your SaaS Responsibilities and Risks

Microsoft’s Shared Responsibility Model: What You Need to Know